The technique of protecting electronic systems, computers, mobile device networks, data, and servers from hostile intrusions is known as cyber security. The value of cybersecurity keeps growing as there are more people, devices, and programs in the modern company, along with an expanding flood of data. It is often referred to as electronic information security or information technology security. The issue is made even worse by the increase in the quantity and level of sophistication of cyberattackers and attack methodologies. As a result, the team may be broken down into a few generic types and applicable across a range of settings, including business and mobile computing.
The Different Types of Cybersecurity :
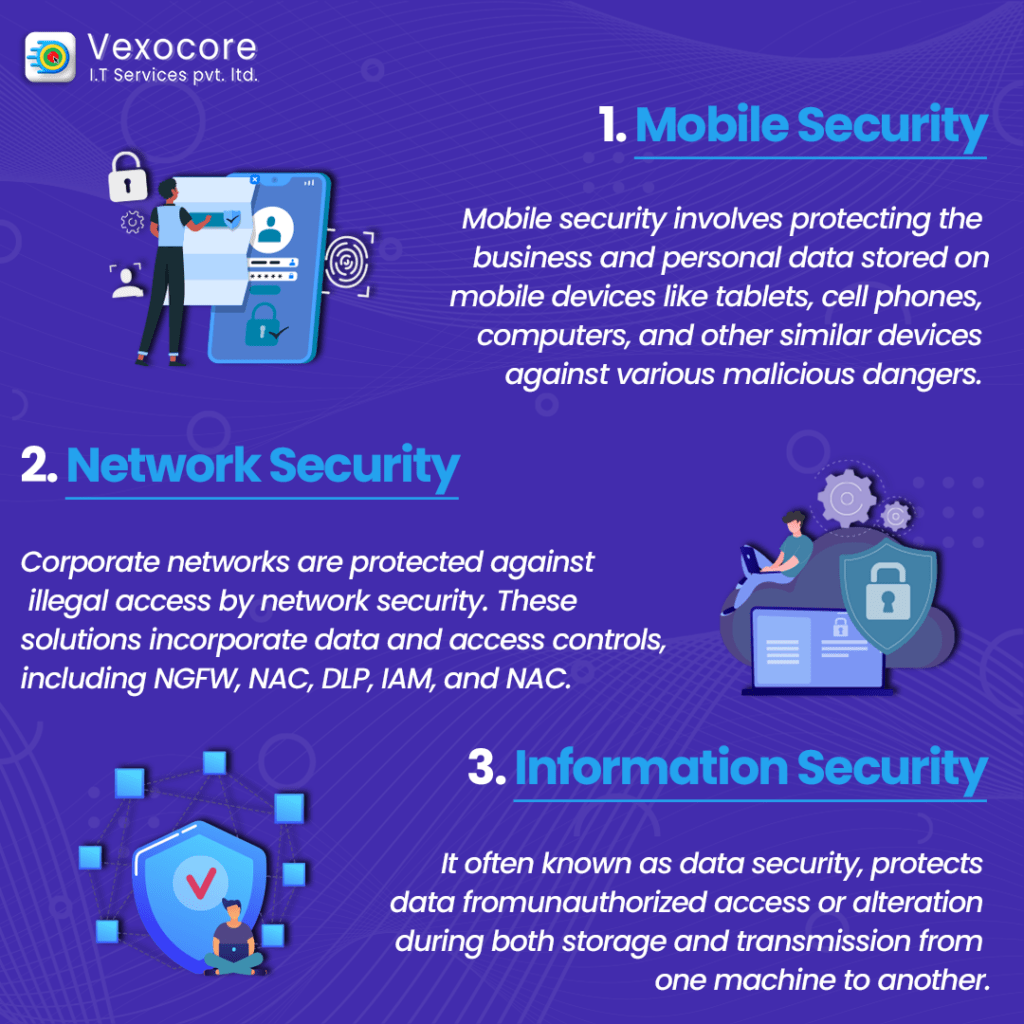
Mobile security involves protecting the business and personal data stored on mobile devices like tablets, cell phones, computers, and other similar devices against various malicious dangers. Mobile security prevents these attacks and secures operating systems and devices from rooting and jailbreaking. This enables businesses to guarantee that only compliant mobile devices have access to company assets when combined with an MDM (Mobile Device Management) solution. These dangers include malware, unauthorized access, device loss or theft, etc.
Corporate networks are protected against illegal access by network security. These solutions incorporate data and access controls, including Next-Generation Firewall (NGFW) application restrictions, Network Access Control (NAC), Data Loss Prevention (DLP), Identity Access Management (IAM), and NAC (Identity Access Management), to enact safe online use regulations.
Information security, often known as data security, is the process of putting in place a reliable data storage system to protect the confidentiality and integrity of data while it is in storage and being sent. protects data from unauthorized access or alteration during both storage and transmission from one machine to another.
Operational security, or OPSEC for short, is the process by which organizations evaluate and safeguard publicly available information about themselves that, if skillfully analyzed and compiled with other information by a cunning adversary, might reveal a more significant picture that ought to remain secret. It entails analyzing data assets and making choices about how to handle and secure them.
Application security prevents bot attacks and other harmful interactions with applications, and APIs and refers to security measures taken at the application level to guard against data theft or code piracy. The OWASP Top 10 dangers can be avoided by using application security. Apps will continue to be secure with continuous learning even as DevOps adds new information. It includes security considerations that take place throughout application development and design, as well as systems and methods to safeguard apps after they are put into use.
Conclusion.
Businesses can rest easy knowing that their network and data are secure, thanks to cyber security. Benefits accrue to organizations, end users, and staff members.
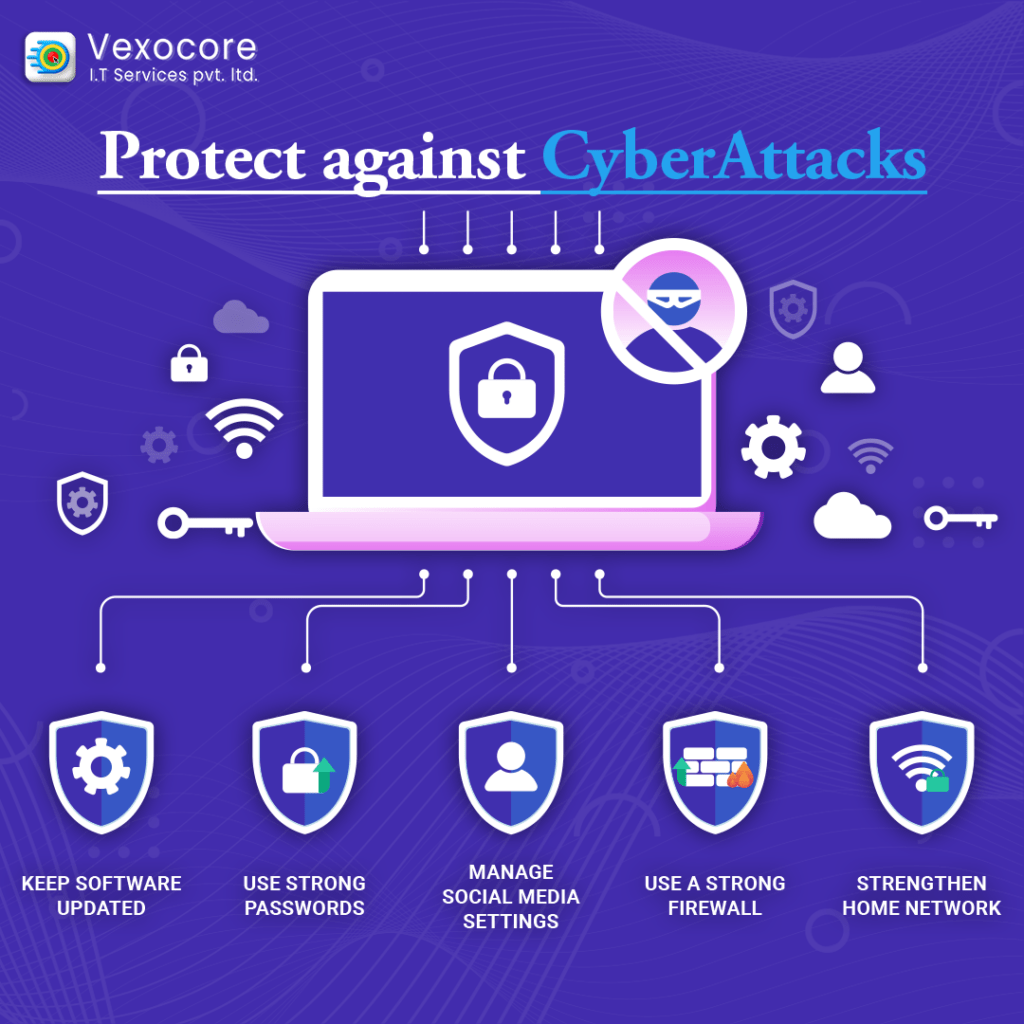
Vexocore (+91 89291 75500 , +91 87662 31429) is one of the leading websites. They offer B2B solutions that are quick and affordable. Therefore, organisations and individuals may defend themselves and others against the whole spectrum of cyber security dangers listed below by installing security solutions.
We recommend you these articles :
what-is-cyber-security-types-careers-salary-and-certification.html
ibtimes.com/partner/why-cybersecurity-should-business-priority-2023-
cyber-security/what-is- cyber security
/what-types-of-jobs-are-available-in-cyber-security/